By Kevin D. Murray - CPP, CFE, BCFE
¡°Should we be checking check for bugs and wiretaps, or am I just being paranoid?¡±
This thought would not have occurred to you if everything were fine. Trust your instincts. Something is wrong. Eavesdropping is a common practice; so are regular inspections to detect it. Conduct an inspection, quickly.
WHAT YOU NEED TO KNOW
Trust Your Instincts
With eavesdropping and espionage, the thought would not have crossed your mind if a real problem did not exist.
Realize That Only Failed Espionage Gets Discovered
You never hear about successful eavesdropping or espionage attacks. You¡¯re not supposed to. It¡¯s a covert act. Eavesdropping and espionage is invisible. Discovery relies heavily on the victim¡¯s intuition and preparedness to handle the problem. Prevention¡ªvia regular inspections¡ªis the logical and cost-effective solution.
Spying Is a Common Activity
Due to the covert nature of spying, the exact extent is not known. Fortunately, however, we can use the failed espionage attempts as a gauge. They reveal over and over again that the problem does exist. Also, the plethora of electronic surveillance equipment being openly sold from Internet ¡°Spy shops¡± gives us a good indication of the magnitude of electronic eavesdropping.

Eavesdropping and Espionage Can Cripple or Kill a Company
Documented cases of eavesdropping and espionage have shown repeatedly that, left unchecked, espionage will eventually desiccate a bottom line, wipe out a competitive advantage, and leave a company a shell of its former self.
Espionage Is Preventable
Information is like any other corporate asset. Management has a responsibility to protect it. Stockholders can claim negligence and hold company executives responsible if this asset is lost due to improper protection efforts. Simple LAG (Locks, Alarms & Guards) are not adequate protection.
The Law Only Protects Those Who Protect Themselves
You can¡¯t just wander into the courtroom crying, ¡°They stole my business secrets¡± and expect help. You have to show the extraordinary steps you took¡ªand maintained¡ªto elevate your business information to secret status.
Counterespionage Is Not a Do-It-Yourself Project
• Don¡¯t buy eavesdropping detection gadgets.
• Don¡¯t play detective.
• Don¡¯t hire a private detective and let them play debugging expert.
This is serious business. Counterespionage work is a full-time specialty within the security field. Professional help is available.

Figure 1. Thermal Emissions Spectrum Analysis (TESA) reveals two spycams and a battery hidden behind a ceiling tile. (Source: Murray Associates)
HOW TO GET HELP
Contact an independent security consultant who specializes in electronic eavesdropping detection and espionage prevention. Recognizing this person may not always be easy.
• Contact several corporate security directors. See whom they are using. Get first hand recommendations.
• Contact industry associations for referrals¡ªe.g., International Association of Professional Security Consultants (www.iapsc.org); Espionage Research Institute (http://www.espionbusiness.com).
• Conduct an Internet search using key words like ¡°avesdropping¡± or ¡°counterespionage¡± Or, visit www.counterespionage.org.
HOW IT¡¯S DONE
Background Interview
Upon arrival the consultant should conduct a background interview with you to obtain an overview of your security concerns¡ªthis discussion will not be held within the areas to be inspected.
Survey of Current Security Measures
This includes an inspection of perimeter and interior physical security hardware.
Visual Examination
The areas in question should be visually inspected for all types of current electronic eavesdropping devices and evidence of past attempts.
Acoustic Ducting Evaluation
Unexpected sound leakage into adjacent areas has been found to be the cause of many information leaks, especially the in-house type.
Inspection of Telephone Instruments
An extensive physical examination of the telephone instruments must be undertaken. There are more than 16 types of attacks involving bugs, taps, and compromises that can be made on a basic telephone instrument¡ªaccording to National Wiretap Commission Report. The newer, electronic telephones have other vulnerabilities, some of which are simple system features that can be abused.
Inspection of Telephone Wiring
Wiring associated with the telephones under test is inspected for attachments and damage. Damaged wiring is often the only evidence of a prior wiretap.
Electronic Testing for Analog and Digital Wiretapping
Special instrumentation is required for these tests¡ªe.g., TALANTM Telephone and Line Analyzer.
Inspection of Telecommunications Junction Blocks
Junction blocks are where telephone wires connect to each other in the building. These connected wires form a path between the telephone instrument and the on-premises, telephone switching equipment. In some cases¡ªe.g., simple residential phone service and facsimile machines¡ªinternal wiring connects directly to outside cables which lead to the phone company central office. Junction blocks are an easy, and relatively safe, place to attach a wiretap device.
Communications Room Inspection
The building communications room houses the junction blocks for the internal phone system, switching equipment for the internal telephone system, telephone company junction blocks for the incoming lines and computer local area network wiring. This is a major area-of-vulnerability requiring inspection from both a wiretapping and physical security point of view.
Non-Linear Junction Detection Inspection (NLJD)
This detection technique is used in sensitive rooms to locate bugs, voice recorders, spycams and amplified microphones that may not be operating at the time of the inspection.
Radio Frequency Spectrum Analysis
Eavesdropping devices may transmit a radio signal¡ªover-the-air, or on building wiring. They are detected with an instrument called a spectrum analyzer (US$10,000 to US$110,000). In simple terms it can be thought of as a radio which has a very long, and continuous, tuning dial. The received signals are shown on a display screen for visual analysis, and are also converted to sound and picture. Each signal is individually evaluated to determine if it is carrying voice, data or video information from the area.
Thermal Emissions Spectrum Analysis
Electronic eavesdropping devices and covert spy cameras are discovered with speed and certainty thanks to a relatively new detection method¡ªThermal Emissions Spectrum Analysis£— (TESA). TESA allows hidden bugs and spy cameras to be ¡®seen¡¯ on a portable video display by virtue of the minute amounts of heat radiated as electricity flows in their circuitry.
Surveillance devices hidden in ceiling tiles, in walls and in other common objects create warm spots. TESA sees these areas even if they are only 18-thousandths of a degree Celsius different in temperature from the surrounding area less than the amount of heat your fingertip leaves on an object after you touch it for a split second.
Additional Tests
As in the medical profession¡ªeavesdropping detection specialists also have many tests that are applied depending upon a client¡¯s specific needs or concerns. Each situation is a bit different. There is, of course, the core group of the aforementioned inspection procedures. Additionally, there are tests that are used as the situation demands. This forces the consultant to add ¡°thought¡± to your inspection process. The overall goal should always be ¡°solve your concerns¡± not simply dash blindly through a checklist.

Final Report
When the inspection is over, you should receive a full verbal debriefing. In this meeting your consultant will highlight all serious problems found, and will recommend solutions which need to be implemented immediately. You should also receive a written report within a week. It should include:
• A description of all the areas and communications equipment inspected;
• An explanation of all tests conducted;
• The findings;
• Recommendations for security improvements;
• A review of other espionage loopholes found;
• Notation of security improvements made since the last inspection; and,
• Counterespionage tips for deterring future attacks
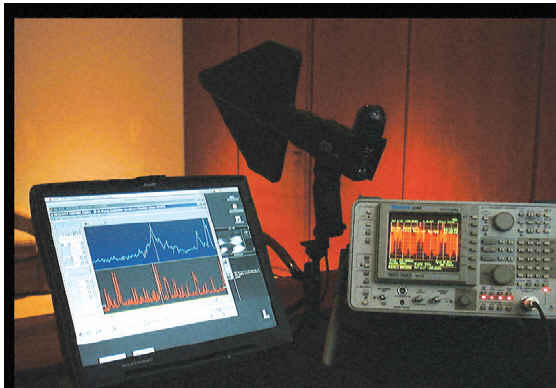
Figure 2. Radio Reconnaissance Spectrum Analysis (RRSA ) locates audio, video and data bugs. (Source: Murray Associates)
BE PREPARED
Electronic spying is a serious economic and privacy concern in corporations and government agencies. Current security best-practices suggest offices, conference rooms, and other sensitive areas undergo eavesdropping detection inspections two to six times per year. Executives¡¯ home offices, vehicles and off-site meeting locations are vulnerable as well and should be checked, too.
Businesses are no longer waiting for eavesdropping problems to surface. Establish your inspection program before a problem surfaces. Inspections need to be conducted regularly to:
• Detect spying before their efforts become problems;
• Protect individual privacy and personal safety;
• Limit windows-of-vulnerability;
• Satisfy on-going legal requirements for due diligence;
• Establish the legal eligibility requirement for business secret status in court; and,
• Identify new methods of privacy invasion and information theft
Unfortunately, not re-inspecting periodically may be interpreted as an admission that previously protected information is no longer important.
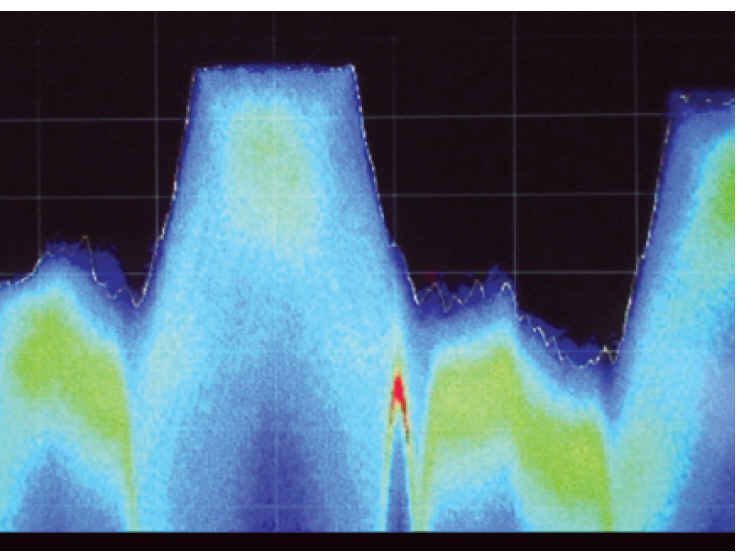
Figure 3. Second Generation RRSA sees bugs hiding behind stronger signals a Murray Associates execlusive capability. (Source: Murray Associates)

NO LONGER HELPLESS
Congratulations! Your security knowledge is now more complete than ever before. No longer will you be powerless to protect your company¡¯s ideas, plans, strategies, hard work, and privacy. No longer will you stand helpless as the opposition tries to pick your pockets. No longer will you live in fear that stockholders will revolt, and judges won¡¯t take you seriously.
Even better. You will not have to stand by and wonder if your electronic eavesdropping sweeps are being conducted properly. You now know the qualities to seek when enlisting the aid of professional counterespionage counsel.
Kevin D. Murray is a BCFE (Board Certified Forensic Examiner); a regular Board Member of the International Association of Professional Security Consultants (IAPSC); on the advisory board of the Espionage Research Institute (ERI); and is CPP (Certified Protection Professional) of ASIS (American Society for Industrial Security). |