By Howard Marson
|
|
|
Secure visitor management systems are rapidly replacing the outdated and low security paper guest logs found in most buildings today.
(Photo by EasyLobby, Inc.) |
Show of hands: how many of you have visited a building where you are asked to sign a paper guest log? OK, now how many of you have signed ¡®Mickey Mouse¡¯ to see if anything would happen? Chances are, nobody noticed. And that is one of the biggest security issues with the paper guest log. Yes, it is very inexpensive and very easy to use, but when it comes to security and today¡¯s mandate to keep track of who is in your buildings and why, the old paper and pen method fails miserably. Now, how many of you are still using a paper guest log to track visitors to your own buildings? And what about that generic hand-written badge you ask the visitor to stick on his/her lapel? Not only does it look bad, but it is also very easy to copy, which means just about anyone could create their own ¡®Valid¡¯ visitor badge and waltz right on in.
In today¡¯s elevated security environment, the paper guest log for visitors and contractors has a number of critical shortcomings:
-
You can¡¯t always read people¡¯s handwriting.
-
You can¡¯t collect detailed, accurate information (not enough space).
-
You can¡¯t capture a photo of the visitor.
-
The information about who is visiting whom is not confidential; it is sitting there for any other visitor to look at.
-
People can make up an employee¡¯s name to get into the building, or just copy the name of an employee that someone else wrote.
-
In the event of an emergency, you cannot quickly pull together a list of who is still in the building (especially if you can¡¯t read people¡¯s names).
-
Hand-written, generic badges are too easy to copy.
-
This method does not instill a sense of security in either visitors or employees.
A BETTER WAY TO MANAGE YOUR VISITORS
|
|
|
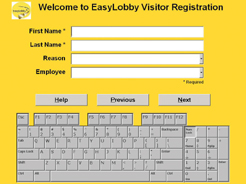
Secure visitor management systems are rapidly replacing the outdated and low security paper guest logs found in most buildings today. (Photo by EasyLobby, Inc.) | About eight years ago, software companies started developing a computerized way to process visitors more accurately, quickly and easily. The goals of these systems were to improve security, and also to enhance the customers¡¯s image by enabling them to more professionally deal with visitors. With a standard personal computer and an inexpensive label printer, these systems allowed you to fill in a simple visitor form on the screen, then print a high-quality, customized badge for each visitor. Since all visitor information was stored in a database, these early ¡®visitor management systems¡¯ also allowed you to do quick searches and print reports with just a few mouse clicks. The information about each visitor was detailed, accurate, and kept confidential (only the guard or receptionist can view the data, not the visitors).
Over time, these systems have continued to evolve and add features, making them even more secure, easier to use, and faster. Today, the leading visitor management systems are integrated with a number of peripheral hardware devices such as passport scanners, driver¡¯s license readers, business card scanners, digital cameras, electronic signature capture pads, and barcode scanners.
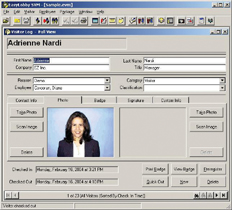
Rather than having to type each visitor¡¯s information into the system, you can now scan or read their passport/driver¡¯s license/business card to automatically capture their name, company, title, phone, email, address, license number, expiration date, date of birth, etc. -- all within just a few seconds. Some of these devices will even capture the photo off the license or passport, as well as a copy of the ID, and store them in the visitor record. You can even print the visitors¡¯s photo on the badge, in full color.
The use of a camera also allows you to capture the visitor¡¯s photo. And for places of business where visitors are required to read and agree to a Non-Disclosure Agreement or Rules and Regulations statement, or any other document, the more sophisticated visitor management systems also allow you to capture the visitors signature electronically as part of the visitor record, and link that signature to the type of document that was read and agreed to.
The better systems also now enable you to print barcodes on the visitor badge, allowing you to simply ¡®scan¡¯ each visitor¡¯s badge on the way out, so the system can track the date and time that they left and keep an accurate record of who is still in the building.
OTHER VALUE-ADDED FEATURES
Custom Badge Design
If you have numerous tenant companies in your building, wouldn¡¯t it be nice to be able to print each company¡¯s logo, in full color, on their visitors¡¯ badges? Or perhaps you¡¯d like to have the name of the employee being visited on the badge, or their photo. Or maybe you want to print the expiration date/time on the badge, or the type of visitor, or the areas they allowed to access. All of these things are possible with a full-featured visitor management system.
Web-based Pre-registration
In addition to the basic features of information capture, badge printing, monitoring and reporting, today¡¯s higher end visitor management systems also allow any or all of your employees to pre-register their visitors via the internet or intranet. Some visitor management companies will even host this service for you on their own web servers if you are in a building that does not have a web server.
Access Control Integration
If you have an access control system in place for employees, or if you have turnstiles that restrict access to an elevator bank or other area of the building, it might be convenient/necessary to be able to give certain visitors automated access. This can be done through integrating the visitor management system and the access control system.
Security Alerts
The more advanced visitor management systems will also provide you with a number of programmable security alerts. One such necessary alert is a Watch List, which checks each visitor¡¯s name against a list of people who should not be allowed to enter the building (ex-employees, estranged spouses, etc.), and alerts the guard or receptionist when a match is found, telling them how to handle the situation. Other useful alerts might include emailing the employee being visited whenever a visitor is checked in for them, or alerting security that someone who is still on the premises has an expired badge.
Employee List
A full-featured visitor management system will also provide you with a method for automatically importing and updating your employee list, so that when a visitor is checked in, you can drop down a list of employees to quickly indicate who they are visiting. The employee list could reside in your access control system, your HR database, or in Active Directory or some other file.
Networking to A Central Database
Your building may have multiple entries as well as a loading dock that you want to cover with tighter visitor control. In this case, the visitor management system should be able to be networked from multiple locations to share a central database over your network. Alternatively, you might have multiple buildings in a campus environment with the same need to share a central visitor database.
Secure visitor management systems are rapidly replacing the outdated and low security paper guest logs found in most buildings today, including K-12 schools, colleges and universities, hospitals and museums, commercial and residential multi-tenant buildings, and government and corporate offices. With a full-featured visitor management system, whether you have a single building with one entry, or 100+ facilities around the globe, you can process visitors in 10-20 seconds by automatically reading a driver¡¯s license or business card, you can print a professional-looking badge with company logo and visitor photo and any other information, you can run reports and query the database, your employees can pre-register their visitors via the internet/intranet, and you can keep unwanted people out of your building(s). But perhaps most importantly, your visitors and employees will feel safer, knowing that each visitor is being properly screened before being allowed to enter.
Howard Marson is CEO of EasyLobby, Inc. (www.easylobby.com)
For more information, please send your e-mails to swm@infothe.com.
¨Ï2007 www.SecurityWorldMag.com. All rights reserved.
|